The knotty problem of data breaches
Security threats are growing in number and complexity, rendering old counter-measures ineffective
 Premium
Premium
Last month, people in India woke up to the news about the largest data breach in the country. It involved data stolen from 3.2 million debit cards between 25 May and 10 July from a network of bank ATMs, managed by a Japanese payment services company. However, the breach was reported in the media only on 21 October.
This fraud is simply a case in point. It was only this January, for instance, that the data of over 7 million users of the mobile edition of the popular game Minecraft was breached. In May, Time Inc. admitted that Myspace—a social networking site it owns—was hacked. In July, US presidential candidate Hillary Clinton’s campaign network was breached by hackers targeting several large Democratic organizations. And, in September, Yahoo Inc. confirmed that data associated with at least 500 million user accounts may have been stolen in what was touted as the largest (by the number of affected users) cybersecurity breach ever.
A November survey by Accenture Plc. reveals that in the past 12 months, roughly one in three targeted attacks resulted in an actual security breach, which equates to two to three effective attacks per month for the average company.
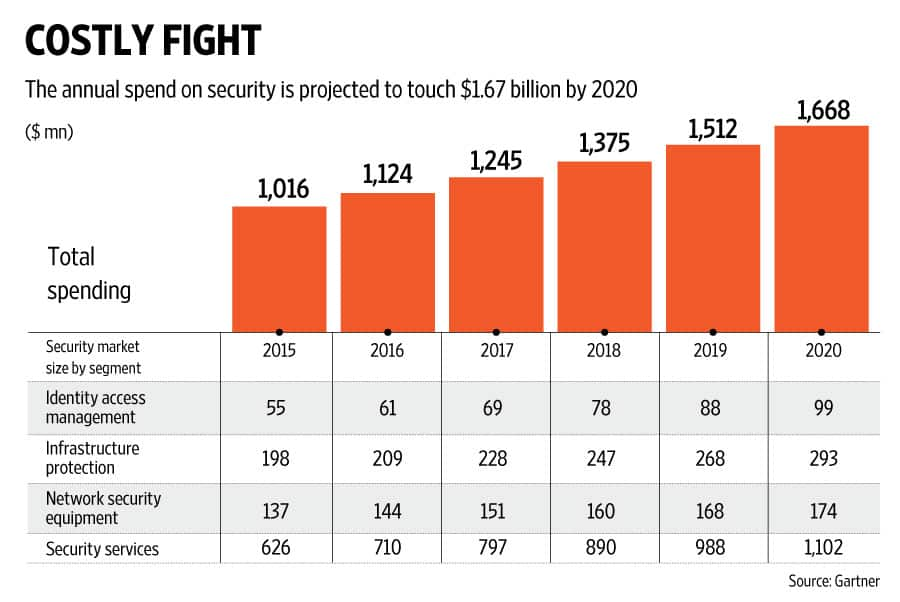
Further, the cost of these breaches is only increasing. According to the 2016 Cost of Data Breach Study: Global Study by Ponemon Institute LLC, the average total cost of a data breach rose from $3.79 million in 2015 to $4 million in 2016. The study also reports that the cost incurred for each lost or stolen record containing sensitive and confidential information increased from a consolidated average of $154 to $158.
The damage is made worse by the length of time it takes to detect and respond to breaches.
In a report by Accenture titled Building Confidence: Facing the Cybersecurity Conundrum, which surveyed 2,000 enterprise security practitioners representing companies with annual revenues of $1 billion or more in 15 countries, more than half of the respondents (51%) disclosed that it takes months to detect sophisticated breaches—and a third of all successful breaches are not detected at all by the security team.
Analysts and security experts concur that security threats are rising in number, complexity, sophistication and impact—often rendering the existing counter-measures ineffective.
“An increasing number of security technologies are being put in place by enterprises. While this is necessarily a good thing, clearly, just throwing technology at a cybersecurity problem may not always help in ensuring that the ends are met and the company is secure," said Burgess Cooper, partner, cybersecurity at EY LLP, a consulting and advisory firm. Of particular importance, he added, is that the people who implement and install the technology tools should be well trained.
The cloud computing model has made security only more complex. Cloud is a metaphor for services provided on a network, primarily the Internet. According to the RightScale 2016 State of the Cloud report, 82% of enterprises have a hybrid cloud (mix of an on-premise and pure cloud) strategy.
“I think we are going to live in this hybrid world for a while, where we have some technologies on-premise and others on the cloud. The level of security will depend on the maturity of a company and its dedicated staff who really understand security as well as business processes," said Hugh Thompson, chief technology officer, Symantec Corp., a global provider of security solutions.
Companies need to balance the need to embrace trends such as cloud and BYOD (bring your own device) with the mandate to safeguard data. One way to tackle the problem, said Thompson, is to be able to wrap a document that has to be shared on the cloud in some encryption so that it can be authenticated before access.
For chief information security officers (CISOs), the big question is how to do an appropriate risk assessment of IT infrastructure, including the tools for cloud and mobility. To get more visibility into the multiple alerts coming in from various security solutions and to get a unified view of their ‘security situation’, a new security management tool called SIEM (security information and event management) has come into vogue. But the key issue, according to Cooper, is whether such tools are being monitored effectively and whether the alerts are being assigned the right priorities.
“What I see now is cyber defence centres coming up, which are much enhanced versions of the plain vanilla SIEMs, wherein they have overall threat intelligence as a weaved-in capability. They have ‘active hunting’ capabilities to figure out what information about a company is available out there on the darknet, on the general Internet, or on sites where hackers normally prowl," said Cooper. In other words, active hunting is a proactive rather than reactive approach to security.
More media coverage of security breaches in recent times has only made board members more aware of cyberthreats; they now want to know about the risks and what their organization needs to do, according to Cooper.
Thompson concurs that for effective cyber security, CISOs will need to look beyond basic SIEMs. He likens most SIEM tools currently in use to what he terms the “car alarm syndrome". He explains, “Most of the time that a car alarm goes off is not when someone is breaking into the car. So, over time, people just get desensitized to the sound of the alarm."
Experts also point out that the big innovations in security are coming from emerging technologies such as big data analytics, machine learning and artificial intelligence. They are being put to use against what are called targeted attacks, which aim at specific individuals rather than the traditional carpet-bombing through phishing. In phishing, lucrative-sounding messages are sent to millions with the intent of stealing user credentials.
To counter such attacks, security firm Symantec, for one, is working on its so-called Project Dolphin that uses hashing techniques combined with machine learning to filter and flag suspicious URLs (universal resource locators, the web addresses users type into browsers to access sites). Under this, the images from the screenshots of popular websites are ‘hashed’ or chopped into smaller pieces and matched with the image of the site a user is trying to access.
Thompson says a machine-learning classifier decides whether a screenshot depicts a phishing target based on similar known phishing screenshots.
As Digital India gains more traction, and the consumer and Industrial Internet of Things trends become more mature, security is bound to pose more challenges, caution experts.
Unlock a world of Benefits! From insightful newsletters to real-time stock tracking, breaking news and a personalized newsfeed – it's all here, just a click away! Login Now!